Don’t Fall for Device Code Phishing!
The Latest Trick from Cybercriminals
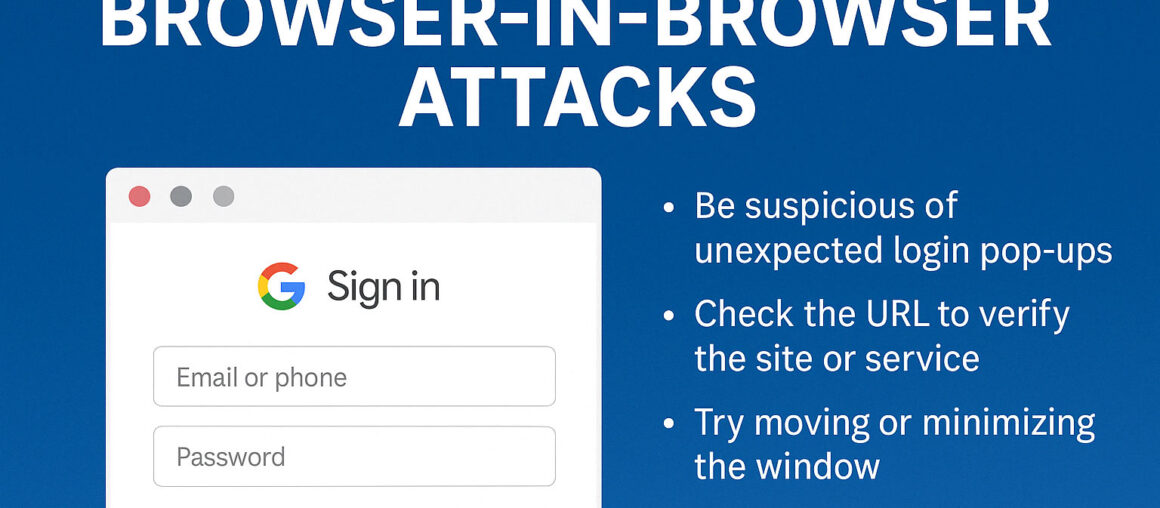
Cybercriminals never stop innovating, and their latest scam targets something you might not expect: the login process on your smart TVs, streaming devices, and even workplace tools. It’s called device code phishing, and it’s designed to trick you into handing over your login credentials through a process that looks completely legitimate.
Here’s what you need to know to stay safe.
What Is Device Code Phishing?
You’ve likely seen it before: a screen on your device that says something like,
“Visit example.com/activate and enter this code to sign in.”
This is known as a device authorization flow, and it’s a normal part of logging into apps on devices that don’t have a keyboard. It’s used by Netflix, Microsoft 365, Google, and more.
But now, attackers are copying that process to phish for your login info. Instead of a real activation page, they set up fake websites that look like the real thing, hoping you’ll enter your code and credentials.
Once you do, they instantly use those credentials on the real service to hijack your account.
How Does the Scam Work?
- You’re prompted with a real-looking activation screen. It may appear on a smart TV, streaming device, or even through a pop-up in a phishing email.
- You visit the link and enter the code. But instead of going to a real site like hulu.com/activate, you’re sent to something like hululogin-verify.com, which is a site controlled by hackers.
- They capture your login info. And now they have access to your streaming account, cloud tools, or even work systems.
Why It’s So Dangerous
- It looks totally legit. These scams mimic real services and processes you trust.
- It bypasses traditional phishing defenses. Since the actual login happens on a separate device, you might not even realize something went wrong.
- It can lead to serious data breaches. If they get into your work or personal accounts, they may access sensitive info, financial data, or worse.
How to Protect Yourself
- Double-check all URLs. Legitimate activation links should be short and familiar (e.g., netflix.com/activate, not netflix-support.tv).
- Don’t scan QR codes or follow links from unexpected sources. Always verify directly on the device.
- Use multi-factor authentication (MFA) such as DUO by Cisco. Even if attackers get your password, MFA can stop them cold.
- Stay skeptical of pop-ups. Especially if they appear out of context or ask you to act fast.
- Educate your family and employees. The more people who recognize this scam, the less damage it can do.
Citynet’s Commitment to Your Security
At Citynet, we know that awareness is your first line of defense against cyber threats. That’s why we regularly share information about the latest scams and security tips, like device code phishing, on our blog and on Facebook and LinkedIn.
For businesses, we go a step further. Our CyberSuite includes powerful tools like security awareness training from KnowBe4, helping your team spot and avoid threats before they cause harm.
If your organization is ready to get serious about cybersecurity, Citynet is ready to help.