Why Immutable Backup Should Be Part of Your Strategy
For small and medium-sized businesses, a single cyberattack can be devastating. Whether it’s ransomware, accidental deletion, or insider threats, losing your data means lost productivity, lost revenue, and in some cases, lost customers.
That’s where immutable backup comes in.
What is Immutable Backup?
Immutable backup means your backed-up data can’t be altered, deleted, or encrypted, even by a hacker or rogue employee. Once your backup is saved, it’s locked in place for a set amount of time. You can restore it, but you can’t tamper with it.
This gives your business a clean, untouchable copy of your data you can rely on, no matter what.
Why It’s Critical for SMBs
SMBs are a top target for ransomware. Why? Because many don’t have the time, staff, or budget for enterprise-grade cybersecurity. Attackers know that. That’s why newer ransomware variants are built to seek out and destroy backups first, forcing businesses to pay up.
With immutable backup, even if your network is compromised, your data is not. You can recover quickly and avoid paying the ransom.
Real-World Benefits for Your Business
- Ransomware Resilience – Your backup stays safe, even if your network is breached.
- Regulatory Compliance – Meet HIPAA, PCI, or other industry requirements with confidence.
- Peace of Mind – You don’t need to wonder if your backups will work when it counts.
- Faster Recovery – Get back up and running without starting from scratch.
- Cost-Effective Protection – Immutable backup is more affordable than you think—and far cheaper than downtime or ransom payments.
How Citynet Protects Your Business
With Citynet, you get:
- Immutable backups as part of our managed backup and disaster recovery plans
- Monitoring and support from our in-house West Virginia-based team
- Flexible cloud or hybrid options to fit your business size and budget
- Expert guidance so you’re never left wondering what’s next
Don’t Wait for a Crisis to Protect Your Data
If your current backup could be deleted, encrypted, or overwritten… it’s not enough. And when disaster strikes, it’s too late to fix it.
Immutable backup gives you the confidence to grow your business, knowing your data is secure.
Let’s make your business ransomware-ready, recovery-capable, and future-proof.
Contact us today or call us at 1.844.CITYNET.








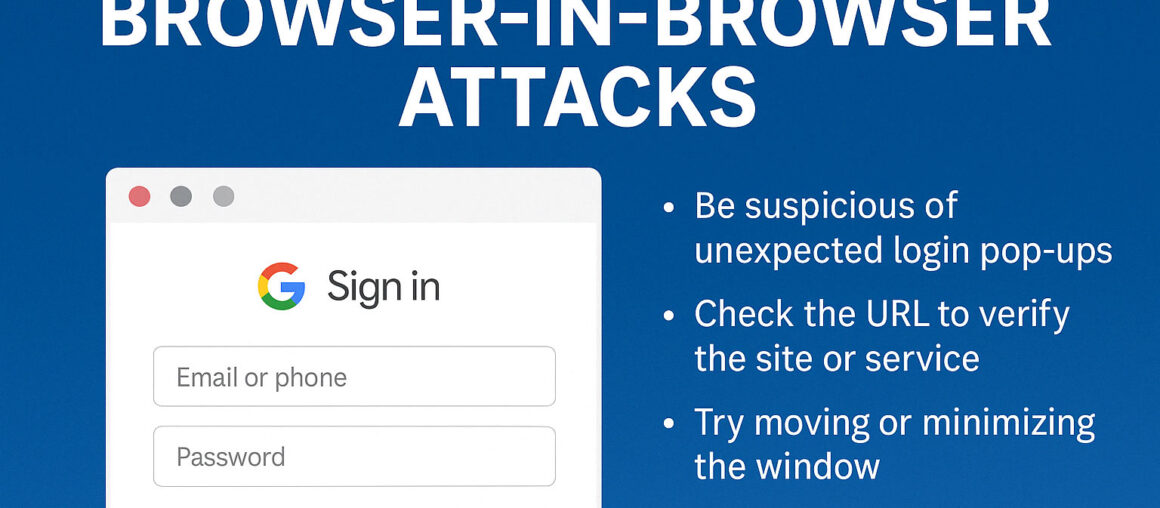

 Huntress is a powerful cybersecurity platform designed to detect and respond to persistent threats that evade conventional security measures. It continuously monitors your IT environment, identifying hidden footholds, unauthorized access, and malware that could compromise your business. With its managed detection and response (MDR) capabilities, Huntress ensures that your organization is protected 24/7.
Huntress is a powerful cybersecurity platform designed to detect and respond to persistent threats that evade conventional security measures. It continuously monitors your IT environment, identifying hidden footholds, unauthorized access, and malware that could compromise your business. With its managed detection and response (MDR) capabilities, Huntress ensures that your organization is protected 24/7.






